
SightLayer: A Technical Overview
1. Introduction
SightLayer is a local-first computer vision system designed to extract useful operational signals from visual environments without retaining or transmitting raw imagery. The system is engineered as infrastructure rather than a surveillance product. Its purpose is to convert transient visual input into privacy-safe textual and numeric summaries that can be aggregated, queried, and analyzed at scale.
The guiding constraints of SightLayer are simple and deliberate: local processing, minimal bandwidth usage, no dependency on cloud inference, and strict avoidance of identity or biometric data. These constraints are not limitations; they are the reasons the system is deployable in real commercial environments.
2. Architectural Philosophy
SightLayer follows a layered architecture in which vision is treated as an input modality, not a stored asset. Cameras exist only as sensors. Images are processed in memory, reduced to abstract representations, and then discarded. The output of the system is not video, frames, embeddings, or facial features. The output is text and structured metadata.
This philosophy sharply distinguishes SightLayer from conventional video analytics systems, which often collect excessive data in anticipation of future use. SightLayer assumes the opposite: if data is not needed for an immediate operational decision, it should not exist.
3. Edge-First Local Processing
Each deployment location runs SightLayer on a local machine. The vision model executes entirely on-site using CPU-friendly inference. This avoids the latency, bandwidth, and privacy risks associated with streaming video off premises.
Local processing ensures deterministic performance regardless of network conditions. It also means each location continues operating independently if connectivity is interrupted. There is no single point of failure tied to a centralized inference service.
From a cost perspective, this design enables deployment on modest hardware. No GPUs are required at the edge, and machines can be selected for reliability rather than raw performance.
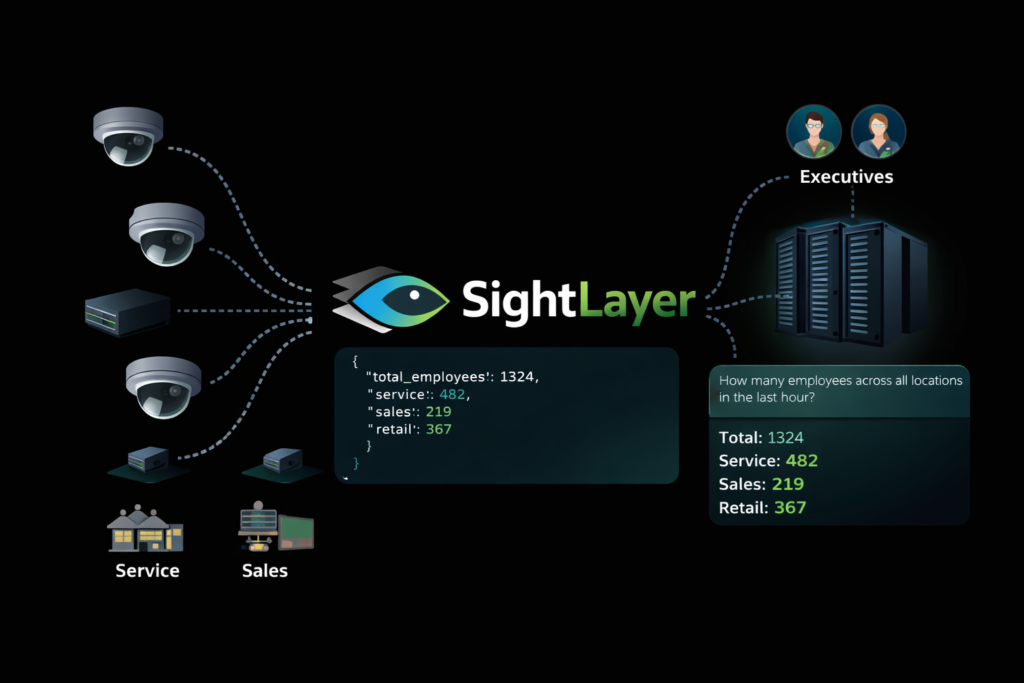
4. Vision-to-Text Pipeline
SightLayer’s core function is image-to-text transformation. Frames are sampled at controlled intervals, analyzed for coarse semantic content such as presence, count, movement, and activity, and immediately reduced into textual summaries or numeric signals.
Examples of outputs include statements like: number of people present, directional flow, dwell time near defined zones, or general activity classification. These summaries are intentionally high-level. They describe what is happening without describing who is involved.
Once the summary is produced, the frame is discarded. No images are written to disk. No embeddings are persisted. This guarantees that the system cannot be repurposed retroactively into an identification system.
5. Privacy by Design
Privacy is not a policy layer added after the fact. It is enforced structurally. SightLayer does not store raw video, does not perform face recognition, and does not track individuals across time or locations.
Because the only retained artifacts are summaries and counts, the system inherently complies with strict privacy expectations. There is nothing to redact, anonymize, or retroactively protect. The data simply does not exist.
This approach reduces legal exposure, simplifies compliance review, and avoids the reputational risks associated with visual surveillance systems.
6. Bandwidth and Network Efficiency
SightLayer is extremely low bandwidth by design. Instead of streaming video or images, each location transmits small textual or structured payloads to headquarters. These payloads are measured in bytes or kilobytes, not megabytes.
This allows hundreds of locations to report frequently without stressing network infrastructure. It also makes secure transmission simpler, since payloads are small, infrequent, and non-sensitive.
The system works equally well on constrained or unreliable networks, which is critical for geographically distributed deployments.
7. Central Aggregation Without Cloud Dependence
The central system aggregates summaries from all locations. This aggregation layer runs locally at headquarters and does not rely on third-party cloud services. All data remains within the organization’s control.
The aggregation layer provides global views such as total occupancy, per-location activity trends, time-based comparisons, and operational dashboards. Because the input data is already distilled, aggregation is computationally inexpensive.
This design avoids recurring cloud inference costs and eliminates exposure to external data processors.
8. Scalability Characteristics
SightLayer scales horizontally. Each new location adds one independent processing node. There is no requirement to scale a centralized inference cluster in proportion to camera count.
This makes deployment predictable. Adding locations increases hardware count linearly, not exponentially. It also enables staged rollouts, pilot deployments, and gradual expansion without architectural changes.
Because the interface between edge nodes and headquarters is stable and minimal, future hardware upgrades do not require system redesign.
9. Operational Reliability
By avoiding real-time cloud dependencies and heavy centralized processing, SightLayer minimizes operational failure modes. Each location can be monitored, updated, or serviced independently.
Failures degrade gracefully. If one location goes offline, the rest continue operating normally. There is no cascading failure scenario.
This reliability profile is critical for enterprise environments where downtime and uncertainty are unacceptable.
10. Queryable Operational Intelligence
Once summaries from all locations are aggregated, SightLayer becomes a queryable operational intelligence layer rather than a passive analytics system. Because the output is already distilled into text and structured metadata, the system can answer natural, executive-level questions directly.
For example, a CEO or operations lead can ask how many people are currently present across all locations. SightLayer can respond with a single total number, derived from live edge reports, without referencing any images or identities. The same query can be broken down by functional zones, such as service bays, sales floors, or retail areas, providing an immediate operational snapshot.
The system can also answer time-bounded questions. Queries such as how many people have been seen in the past hour, how many entered or exited during a defined window, or how activity levels compare to the same time last week are answered by aggregating summaries over time rather than replaying footage.
Because SightLayer understands zones and activity categories, higher-level breakdowns are possible. Examples include counts of customers currently in service versus sales, general dwell time near retail displays, or overall foot traffic trends during promotions. These answers are produced from structured summaries, not retrospective video analysis.
SightLayer can also surface workforce-related signals without identifying individuals. For example, it can estimate how many employees have been present during a time window, whether staffing levels appear consistent with expected demand, or whether certain areas are understaffed based on observed activity density.
All of these responses are generated without exposing or storing raw visual data. The system does not need to reprocess images to answer new questions. The summaries already contain the necessary signal, which makes responses fast, inexpensive, and privacy-safe.
11. Why This System Works
SightLayer works because it aligns technical design with real operational questions. Executives do not want video feeds; they want answers. By converting vision into text and metadata at the edge, the system produces exactly the level of abstraction required to support decision-making.
By treating vision as a transient signal source rather than a stored asset, SightLayer achieves a balance that most systems miss. It delivers actionable insight while structurally preventing misuse. That combination of local processing, queryable summaries, low bandwidth usage, and enforced privacy is what makes the system viable and valuable at enterprise scale.